In the digital world of 2025, cyber threats are evolving faster than ever. Traditional security models — the kind that assume everything inside your network is “safe” — are becoming dangerously outdated. Zero Trust Architecture (ZTA) has emerged as the smarter, more resilient approach, and this year, it’s no longer optional.
If your organization is still relying on perimeter-based security, it’s like locking your front door but leaving all the windows open. Zero Trust changes the game.
What Is Zero Trust Architecture?
Zero Trust is based on a simple but powerful idea: “Never trust, always verify.”
Instead of assuming that users or devices inside your network are safe, Zero Trust requires continuous verification of every access request — no matter where it comes from.
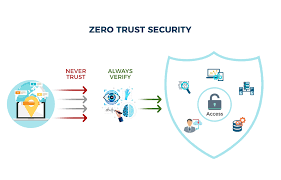
Key principles include:
- Verify Every User and Device – Identity and device authentication for every request.
- Least Privilege Access – Users only get the access they need, nothing more.
- Microsegmentation – Breaking the network into smaller sections to limit damage if breached.
- Continuous Monitoring – Constant tracking and analyzing of activity for unusual behavior.
Why Traditional Security Models Are Failing in 2025
- Remote & Hybrid Work – Employees are logging in from home, cafés, and even abroad.
- Cloud Adoption – Data and apps are spread across multiple platforms.
- Sophisticated Threats – Hackers use stolen credentials, phishing, and ransomware that bypass traditional defenses.
- Insider Risks – Not all threats come from the outside; employees or contractors can unintentionally or maliciously cause breaches.
Perimeter-based models simply can’t handle this complexity.
Case Study 1: Google BeyondCorp
The Problem:
Google wanted a secure framework for employees working from anywhere without relying on traditional VPNs.
Zero Trust Solution:
Google built BeyondCorp, which enforces identity and device verification for every request, regardless of location.
Impact:
- Seamless remote work without sacrificing security.
- Stronger defenses against phishing attacks.
- Improved employee productivity by removing VPN bottlenecks.
Case Study 2: Capital One
The Problem:
Financial institutions face heavy compliance demands and constant cyberattack attempts.
Zero Trust Solution:
Capital One implemented a Zero Trust Architecture approach using identity-based access controls, encryption, and real-time threat detection.
Impact:
- Reduced risk of insider threats.
- Strengthened compliance posture.
- Increased customer trust in digital banking.
Benefits of Implementing Zero Trust
1. Stronger Security Posture
Zero Trust reduces the attack surface by ensuring that no user or device is inherently trusted.
2. Protection Against Credential Theft
Even if a hacker steals a password, they still face multiple verification layers.
3. Improved Compliance
Meets strict data privacy and security regulations like GDPR, HIPAA, and PCI DSS.
4. Business Agility
Supports secure remote work, multi-cloud operations, and third-party collaborations.
How to Implement Zero Trust in 2025
Step 1: Identify & Classify Assets
Know what you’re protecting — data, applications, devices, and users.
Step 2: Strengthen Identity & Access Management (IAM)
Use Multi-Factor Authentication (MFA), biometrics, and Single Sign-On (SSO).
Step 3: Apply Least Privilege Principles
Grant access only to what’s needed and review permissions regularly.
Step 4: Microsegment the Network
Break your network into smaller “zones” to contain breaches.
Step 5: Implement Continuous Monitoring
Leverage tools for real-time threat detection and behavioral analytics.
Challenges to Expect
- Cultural Resistance – Teams may resist changes in workflows.
- Complex Integration – Connecting old systems with Zero Trust tools can be tricky.
- Cost & Resources – Initial setup requires investment in tools and training.
However, in the long run, Zero Trust saves far more by preventing costly breaches.
Why 2025 Is the Year to Act
Cybercrime damages are projected to cost the world $10.5 trillion annually by 2025. With remote work, IoT devices, and AI-powered attacks increasing, perimeter-based security is simply not enough.
Adopting Zero Trust now means:
- Staying ahead of evolving threats.
- Meeting new regulatory requirements.
- Protecting brand reputation and customer trust.
Final Thoughts
Zero Trust Architecture is not just a tech upgrade — it’s a mindset shift. It treats every access attempt as potentially hostile and verifies it. In 2025, this approach isn’t about being paranoid; it’s about being prepared.
For organizations that want to thrive in a connected, complex, and threat-filled world, Zero Trust Architecture is the only security strategy that makes sense.





